阅读完需:约 9 分钟
前面在这个讲了SpringSecurity 基于数据库的认证,但是这个认证中的用户认证是有问题的,因为里面的用户权限都是写死的,很难更改,所以用数据库的动态配置就能解决这个问题!
官方 中文 文档:
https://www.springcloud.cc/spring-security-zhcn.html#core-components
项目总目录:
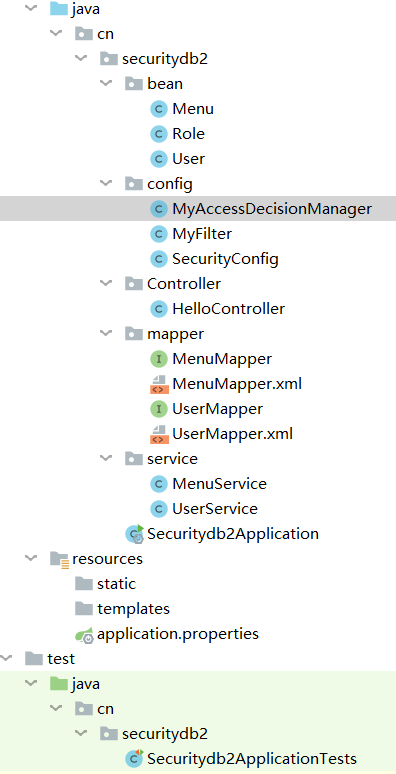
1.首先要创建项目:
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>2.1.2</version>
</dependency>
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid-spring-boot-starter</artifactId>
<version>1.1.10</version>
</dependency>2.连接数据库
spring.datasource.url=jdbc:mysql://127.0.0.1:3306/security
spring.datasource.username=root
spring.datasource.password=123
spring.datasource.type=com.alibaba.druid.pool.DruidDataSourceSQL数据库:
/*
Navicat MySQL Data Transfer
Source Server : root
Source Server Version : 50562
Source Host : localhost:3306
Source Database : security
Target Server Type : MYSQL
Target Server Version : 50562
File Encoding : 65001
Date: 2020-04-12 15:21:18
*/
SET FOREIGN_KEY_CHECKS=0;
-- ----------------------------
-- Table structure for menu
-- ----------------------------
DROP TABLE IF EXISTS `menu`;
CREATE TABLE `menu` (
`id` int(11) NOT NULL,
`pattern` varchar(255) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of menu
-- ----------------------------
INSERT INTO `menu` VALUES ('1', '/dba/**');
INSERT INTO `menu` VALUES ('2', '/admin/**');
INSERT INTO `menu` VALUES ('3', '/user/**');
-- ----------------------------
-- Table structure for menu_role
-- ----------------------------
DROP TABLE IF EXISTS `menu_role`;
CREATE TABLE `menu_role` (
`id` int(11) NOT NULL,
`mid` int(11) DEFAULT NULL,
`rid` int(11) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of menu_role
-- ----------------------------
INSERT INTO `menu_role` VALUES ('1', '1', '1');
INSERT INTO `menu_role` VALUES ('2', '2', '2');
INSERT INTO `menu_role` VALUES ('3', '3', '3');
-- ----------------------------
-- Table structure for role
-- ----------------------------
DROP TABLE IF EXISTS `role`;
CREATE TABLE `role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`name` varchar(32) DEFAULT NULL,
`nameZh` varchar(32) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=4 DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of role
-- ----------------------------
INSERT INTO `role` VALUES ('1', 'ROLE_dba', '数据库管理员');
INSERT INTO `role` VALUES ('2', 'ROLE_admin', '系统管理员');
INSERT INTO `role` VALUES ('3', 'ROLE_user', '用户');
-- ----------------------------
-- Table structure for user
-- ----------------------------
DROP TABLE IF EXISTS `user`;
CREATE TABLE `user` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`username` varchar(32) DEFAULT NULL,
`password` varchar(255) DEFAULT NULL,
`enabled` tinyint(1) DEFAULT NULL,
`locked` tinyint(1) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=4 DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of user
-- ----------------------------
INSERT INTO `user` VALUES ('1', 'root', '$2a$10$RMuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqilXzbz50dceRsga.WYiq', '1', '0');
INSERT INTO `user` VALUES ('2', 'admin', '$2a$10$RMuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqilXzbz50dceRsga.WYiq', '1', '0');
INSERT INTO `user` VALUES ('3', 'sang', '$2a$10$RMuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqilXzbz50dceRsga.WYiq', '1', '0');
-- ----------------------------
-- Table structure for user_role
-- ----------------------------
DROP TABLE IF EXISTS `user_role`;
CREATE TABLE `user_role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`uid` int(11) DEFAULT NULL,
`rid` int(11) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=5 DEFAULT CHARSET=utf8;
-- ----------------------------
-- Records of user_role
-- ----------------------------
INSERT INTO `user_role` VALUES ('1', '1', '1');
INSERT INTO `user_role` VALUES ('2', '1', '2');
INSERT INTO `user_role` VALUES ('3', '2', '2');
INSERT INTO `user_role` VALUES ('4', '3', '3');数据里的各个表:
资源表:
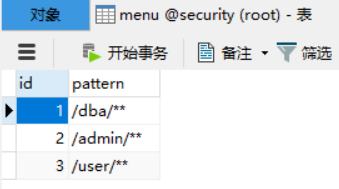
角色表:
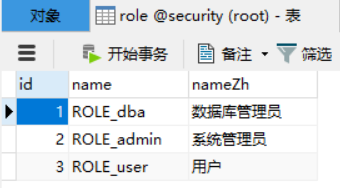
用户表:
用户角色关联表:
资源角色关联表:
3.创建实体类:
第一个User:
public class User implements UserDetails {
private Integer id;
private String username;
private String password;
private Boolean enabled;
private Boolean locked;
private List<Role> roles;
public List<Role> getRoles() {
return roles;
}
public void setRoles(List<Role> roles) {
this.roles = roles;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
@Override
public String getUsername() {
return username;
}
@Override
public boolean isAccountNonExpired() {
return true;
}
@Override
public boolean isAccountNonLocked() {
return !locked;
}
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@Override
public boolean isEnabled() {
return enabled;
}
public void setUsername(String username) {
this.username = username;
}
@Override //返回用户的所有角色 一定一定不要忘记加上 ROLE_ 这个前缀
@JsonIgnore 忽略JSON的序列化,不然会报错
public Collection<? extends GrantedAuthority> getAuthorities() {
List<SimpleGrantedAuthority> list=new ArrayList<>();
for(Role role:roles){
list.add(new SimpleGrantedAuthority(role.getName()));
}
return list;
}
@Override
public String getPassword() {
return password;
}
public void setPassword(String password) {
this.password = password;
}
public void setEnabled(Boolean enabled) {
this.enabled = enabled;
}
public void setLocked(Boolean locked) {
this.locked = locked;
}
}关于UserDetails 接口的解释都在上一篇文章中
第二个Role:
public class Role {
private Integer id;
private String name;
private String nameZh;
@Override
public String toString() {
return "Role{" +
"id=" + id +
", name='" + name + '\'' +
", nameZh='" + nameZh + '\'' +
'}';
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getName() {
return name;
}
public void setName(String name) {
this.name = name;
}
public String getNameZh() {
return nameZh;
}
public void setNameZh(String nameZh) {
this.nameZh = nameZh;
}
}第三个Menu:
public class Menu {
private Integer id;
private String pattern;
private List<Role> roles;
@Override
public String toString() {
return "Menu{" +
"id=" + id +
", pattern='" + pattern + '\'' +
", roles=" + roles +
'}';
}
public List<Role> getRoles() {
return roles;
}
public void setRoles(List<Role> roles) {
this.roles = roles;
}
public Integer getId() {
return id;
}
public void setId(Integer id) {
this.id = id;
}
public String getPattern() {
return pattern;
}
public void setPattern(String pattern) {
this.pattern = pattern;
}
}
4.创建Mapper映射和接口:
UserMapper接口:
@Mapper
public interface UserMapper {
User loadUserByUsername(String s);
List<Role> getRolesById(Integer id);
}UserMapper映射:
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper
PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<mapper namespace="cn.securitydb2.mapper.UserMapper">
<select id="loadUserByUsername" resultType="cn.securitydb2.bean.User">
select * from user where username=#{username}
</select>
<select id="getRolesById" resultType="cn.securitydb2.bean.Role">
select * from role r ,user_role ur where r.id=ur.rid and ur.uid=#{id}
</select>
</mapper>MenuMapper的接口:
@Mapper
public interface MenuMapper {
List<Menu> getAllMenu();
List<Menu> getAllMenuWithRole();
}
MenuMapper的映射:
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper
PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<mapper namespace="cn.securitydb2.mapper.MenuMapper">
<resultMap id="BaseResultMap" type="cn.securitydb2.bean.Menu">
<id property="id" column="id"/>
<result property="pattern" column="pattern"/>
<collection property="roles" ofType="cn.securitydb2.bean.Role">
<id property="id" column="rid"/>
<result property="name" column="rname"/>
<result property="nameZh" column="rnameZh"/>
</collection>
</resultMap>
<select id="getAllMenu" resultMap="BaseResultMap">
SELECT m.*,r.id AS rid,r.name AS rname,r.nameZh AS rnameZh FROM menu m LEFT JOIN menu_role mr ON m.`id`=mr.`mid` LEFT JOIN role r ON mr.`rid`=r.`id`
</select>
<select id="getAllMenuWithRole" resultMap="BaseResultMap">
select m.*,r.`id` as rid,r.`name` as rname,r.`nameZh` as rnameZh from menu m,menu_role mr,role r where m.`id`=mr.`mid` and mr.`rid`=r.`id` order by m.`id`
</select>
</mapper>5.创建Service:
UserService:
@Service
public class UserService implements UserDetailsService {
@Autowired
UserMapper userMapper;
@Override
//根据用户名去查询用户,并返回一个UserDetails
public UserDetails loadUserByUsername(String s) throws UsernameNotFoundException {
User user=userMapper.loadUserByUsername(s);
if(user==null){
throw new UsernameNotFoundException("用户不存在");
}
user.setRoles(userMapper.getRolesById(user.getId()));
try {
System.out.println(new ObjectMapper().writeValueAsString(user));
} catch (JsonProcessingException e) {
e.printStackTrace();
}
return user;
}
}
主要用来查询用户
MenuService:
@Service
public class MenuService {
@Autowired
MenuMapper menuMapper;
public List<Menu> getAllMenu(){
return menuMapper.getAllMenu();
}
public List<Menu> getAllMenuWithRole(){
return menuMapper.getAllMenuWithRole();
}
}查询角色对应的权限资源
6.创建config配置文件:
MyAccessDecisionManager:
@Component
public class MyAccessDecisionManager implements AccessDecisionManager {
//在该方法中判断当前登录的用户是否具有当前请求URL所需要的角色信息,如果不具备,就抛出AccessDeniedException异常,
// 否则不做任何事情
/*
参数:
1. Authentication: 包含当前登录用户的信息
2. Object: 是一个FilterInvocation对象,可以获取当前请求对象
3. Collection<ConfigAttribute>: FilterInvocationSecurityMetadataSource中的getAttributes方法的返回值,
即当前请求URL所需要的角色
*/
@Override
public void decide(Authentication authentication, Object o, Collection<ConfigAttribute> collection) throws AccessDeniedException, InsufficientAuthenticationException {
for (ConfigAttribute attrribute:collection){
if("ROLE_login".equals(attrribute.getAttribute())){
if (authentication instanceof AnonymousAuthenticationToken){
throw new AccessDeniedException("非法请求");
}else{
return;
}
}
Collection<? extends GrantedAuthority> authorities=authentication.getAuthorities();
for (GrantedAuthority authority : authorities){
if(authority.getAuthority().equals(attrribute.getAttribute())){
return;
}
}
}
throw new AccessDeniedException("非法请求");
}
@Override
public boolean supports(ConfigAttribute configAttribute) {
return true;
}
@Override
public boolean supports(Class<?> aClass) {
return true;
}
}
MyFilter:
import java.util.Collection;
import java.util.List;
@Component //这个类是根据你的URL来判断需要什么角色
public class MyFilter implements FilterInvocationSecurityMetadataSource {
//用于实现ant风格的URL匹配
AntPathMatcher PathMatcher=new AntPathMatcher();
@Autowired
MenuService menuService;
@Override
public Collection<ConfigAttribute> getAttributes(Object o) throws IllegalArgumentException {
//获取当前请求的URL
String requestUrl = ((FilterInvocation) o).getRequestUrl();
//获取数据库中的资源信息,一般放在Redis缓存中
List<Menu> allMenu=menuService.getAllMenu();
// 特别注意的是,这里的资源获取的是全部资源,不是根据角色获取的资源,需要做进一步处理,或者使用一下:
List<Menu> allMenu=menuService. getAllMenuWithRole();
//遍历信息,遍历过程中获取当前请求的URL所需要的角色信息并返回
for (Menu menu:allMenu){
if(PathMatcher.match(menu.getPattern(),requestUrl)){
List<Role> roles=menu.getRoles();
String[] rolesStr=new String[roles.size()];
for(int i=0;i<roles.size();i++){
rolesStr[i]=roles.get(i).getName();
}
return SecurityConfig.createList(rolesStr);
}
}
//如果当前请求的URL在资源表中不存在响应的模式,就假设该请求登录后即可访问,直接返回ROLE_LOGIN
return SecurityConfig.createList("ROLE_login");
}
//getAllConfigAttributes()方法用来返回所有定义好的权限资源,SpringSecurity在启动时会校验相关配置是否正确
//如果不需要校验,直接返回null即可
@Override
public Collection<ConfigAttribute> getAllConfigAttributes() {
return null;
}
//supports方法返回类对象是否支持校验
@Override
public boolean supports(Class<?> aClass) {
return true;
}
}
SecurityConfig:
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
UserService userService;
@Autowired
MyFilter myFilter;
@Autowired
MyAccessDecisionManager myAccessDecisionManager;
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userService);
}
@Bean
PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
@Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
.withObjectPostProcessor(new ObjectPostProcessor<FilterSecurityInterceptor>() {
@Override
public <O extends FilterSecurityInterceptor> O postProcess(O o) {
o.setAccessDecisionManager(myAccessDecisionManager);
o.setSecurityMetadataSource(myFilter);
return o;
}
})
.and()
.formLogin()
.permitAll()
.and()
.csrf().disable();
}
}这几个是主要的配置文件,思路是先从Url中获取你需要的角色,再将数据库里的角色返回,进行对比,如果一致就可以访问。
7.创建Controller:
@RestController
public class HelloController {
@GetMapping("/hello")
public String hello(){
return "hello !";
}
@GetMapping("/dba/hello")
public String dba(){
return "hello dba";
}
@GetMapping("/admin/hello")
public String admin(){
return "hello admin";
}
@GetMapping("/user/hello")
public String user(){
return "hello user";
}
}